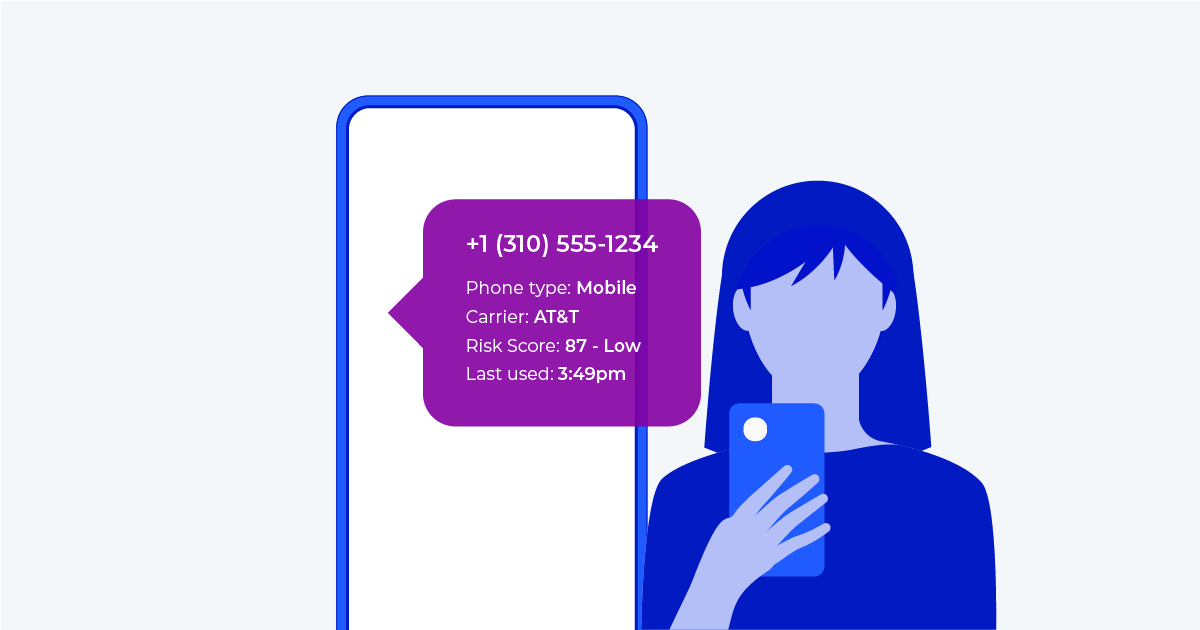
Establishing identity in the digital world poses unique challenges compared to the physical one. Verifying someone in person can be straightforward—people recognize each other, and photo IDs make it easy to confirm who they are. In digital spaces, however, confirming identity is more complex. Businesses must adopt a strategic, multi-layered approach to authenticate users effectively, ensuring both security and trust online.
In today’s digital age, we increasingly rely on online services and electronic communications for critical tasks. Managing finances, scheduling healthcare appointments, and shopping online all require digital identity verification. Without it, the risk of identity theft, fraud, and financial harm grows significantly. Modern businesses need systems capable of verifying digital identities before allowing users to proceed.
Effective identity verification not only enhances security but also creates a seamless, user-friendly experience for customers. As a result, businesses must prioritize the adoption and integration of secure digital identity verification processes. But what does this entail?
This blog explores the fundamentals of digital identity, the reasons businesses need a robust strategy to help verify and protect genuine users, and how you can benefit from advanced solutions available today.
Table of Contents
- What is digital identity?
- Types of digital identity
- Why a digital identity strategy is vital in business
- The benefit of robust digital identity verification
- Verifying digital identities: tools and methods
- Overcoming challenges in digital identity management
- Enhance your approach to verification
- The future of digital identity management
- Explore the best approach for your business today
What is digital identity?
At its core, a digital identity is a unique set of identifiable characteristics that represent an individual online. It provides businesses with information to verify and understand who they are interacting with digitally. Traditionally, digital identity can include something as straightforward as an email and password combination, but modern identities are far more nuanced.
Today, an individual’s digital identity can consist of multiple elements. Although organizations and businesses also have digital identities, in this article, we’ll focus on individual users.
Digital identity plays a central role in authentication and verification processes that grant users access to goods and services online. By verifying a user’s digital identity, businesses protect both users and themselves, ensuring the individual is who they claim to be.
Types of digital identity
A digital identity isn’t a single piece of information or type of data—it’s the combination of multiple signals. Not every identity includes all types of information, but the more signals companies can analyze, the easier it becomes to authenticate users and protect against threats like identity theft. Common examples of digital identity factors include:
- Email addresses
- Usernames and passwords
- Date of birth
- Social Security numbers and unique identifiers
- Phone numbers
- Official document details, such as passport numbers
- Social media profiles
- Personal information (used for account security questions)
- Biometric data, such as fingerprints or facial recognition
Today’s technology can also incorporate more complex behavioral data into a digital identity. Patterns of behaviors across platforms can provide additional insights about users. Other elements that may be part of someone’s digital identity include:
- Web activity
- Digital transactions
- Purchasing history
- Shopping cart behavior, and more
In today’s digital landscape, businesses must have a strategy to understand and authenticate the identities of their users effectively.
Why a digital identity strategy is vital in business
Why is a smart approach to digital identity so crucial for companies today? While the basic need is clear—every business operating online must identify and authenticate its users—there are deeper reasons to craft a strong strategy.
Digital identity plays a central role in both user privacy and overall security. It’s essential for preventing impersonation and account fraud. Identity theft poses a real risk: someone who misrepresents their identity online could cause significant financial harm to both legitimate customers and businesses. A robust digital identity strategy helps safeguard against the many risks present in the online world.
Identity verification isn’t just about protecting a business from unauthorized actions; it protects customers and the entire ecosystem in which the business operates. Compromised identities and weakened trust can have a ripple effect, threatening the security of far more than one individual. Poor security may allow bad actors to infiltrate and manipulate systems, exposing businesses to far greater risks.
By investing in a strong digital identity strategy, businesses can shield themselves from these threats. A smooth and seamless verification process enhances productivity and operational efficiency, improving the overall customer experience and fostering greater trust.
In Okta’s State of Digital Trust report, 23% of respondents said that strong sign-in security greatly impacted their perceptions of trust in a business. This highlights the importance of a well-defined approach to digital identity verification. Without a unified and coordinated strategy, businesses may face security gaps and increased risk.
The benefit of robust digital identity verification
Strong identity management is crucial for preventing crimes like identity theft and safeguarding against the financial risks of fraud. But what other advantages does it offer?
For customers, the benefits are clear. Chief among them is peace of mind regarding the security of their accounts. No one wants to worry about bad actors accessing sensitive information, especially when personal data or credit card numbers are linked to their digital identity. Effective verification minimizes the risk of such information falling into the wrong hands. Even if some account details are compromised, modern solutions such as multifactor authentication (MFA) can help protect against intrusion attempts.
Beyond enhanced security, robust digital identity verification is about finding the right balance. While some friction is necessary to ensure protection against fraud, it’s equally important to streamline processes wherever possible to keep customer experiences smooth and efficient. The right verification measures not only safeguard accounts but can also help simplify onboarding, maintain consistency across channels, and foster personalized interactions that strengthen customer trust and engagement. When businesses strike this balance, robust identity verification doesn’t just protect—it also supports customer satisfaction and adds value to the bottom line.
Verifying digital identities: tools and methods
Today, there are numerous approaches to verifying digital identities, each with its own strengths and weaknesses. A robust strategy often involves combining multiple methods to enhance security. So, what are some of the most common approaches used today?
- Multifactor authentication (MFA): The most widely used method, MFA requires users to provide multiple credentials to verify their identity. For example, entering a username and password might trigger the need for a one-time password (OTP) sent to the user’s phone.
- Biometric authentication: Methods like fingerprint scanning and facial recognition are becoming increasingly popular for certain applications, especially in securing digital devices like phones. However, adoption in business contexts has been slower, primarily due to privacy concerns.
- Document verification: This involves comparing photos of an individual’s identity documents, such as a driver’s license or passport, to confirm their identity.
Technology plays a pivotal role in establishing solid verification procedures and Telesign offers solutions that make a significant impact in these areas. Our products that align with the need to secure your digital ecosystem include:
- Intelligence: Leverage machine learning and AI to analyze the risk of interactions from new and existing accounts. Analyze digital identity signals to detect possible fraud attempts and behavior that deviates from known, legitimate user patterns.
- Phone ID: Understand the legitimacy and risk of the phone numbers that interact with your business by accessing static and behavioral phone number attributes including location details, porting history, SIM swap status, and more.
- Verify API: Seamlessly authenticate users on their preferred communication channels with our Verify API that provides access to 7 channels through one API endpoint and adds a critical layer of protection to your digital ecosystem by confirming user identity before sensitive actions occur.
Overcoming challenges in digital identity management
As you work to create a secure environment for your business while maintaining a positive user experience, challenges may arise. Anticipating these obstacles allows you to better plan and navigate around them. Some common challenges include:
- User concerns about security and privacy: In a survey of smartphone users by Deloitte, 67% said they worry about both security and privacy on their devices. The increasing number of data breaches adds to these worries.
- Challenges with technology integration: Updating or upgrading your systems to support modern identity verification may require a more detailed plan and extra time.
- Concerns about user adoption: Will your users embrace the new system and find it helpful, or will it lead to issues?
- Regulatory compliance: New data privacy laws such as the General Data Protection Regulation (GDRP), have been introduced in recent years. Ensuring your system delivers compliant service is crucial.
Solutions exist for all these challenges. Adopting a stringent, security-focused approach and providing a transparent privacy policy can safeguard user information. Partnering with the right technology providers, like Telesign, can simplify integration, while a streamlined user experience fosters adoption. Staying proactive about evolving regulations helps you avoid costly surprises.
Enhance your approach to verification
Through solutions such as Telesign’s Verify API, businesses can explore various pathways to implement effective MFA implementation. MFA has become a cornerstone of digital identity strategies, leveraging the universal reach of mobile phones to provide authentication for nearly every user.
How can you approach identity verification with Telesign?
- Send one-time passcodes (OTPs): The Verify API makes it easy to authenticate users by reaching them through their preferred communication channels. This includes common methods like SMS and email, as well as more advanced channels such as RCS, and over-the-top (OTT) messaging apps such as Viber and WhatsApp.
- Leverage silent verification: Authenticate users seamlessly in the background by instantly matching the user’s phone number with Mobile Operator Network data to verify that a user is in possession of the device, all without requiring any action from the user.
- Use push notifications: Send authentication prompts via mobile push notifications, allowing users to verify their identity with just a quick tap.
Telesign prioritizes regulatory compliance, supporting businesses in implementing effective, compliant strategies even in a complex environment. Our advanced fraud detection capabilities help mitigate risks and block potential fraudsters. Moreover, our services are scalable, from small businesses to large international operations.
The future of digital identity management
The importance of strong digital identity management will only continue to grow. In the near and long term, businesses will face increasingly complex needs and an evolving threat landscape. The expansion of digital data regulations will also likely impact how brands provide secure yet seamless experiences. So, what should we anticipate in this area?
- The growth of the self-sovereign identity
Self-sovereign identity (SSI) is an emerging approach to digital identity management. With SSI, individuals gain significantly more control over their online information than ever before. Instead of relying on centralized authorities to share verifiable identity credentials, SSI allows users to choose what credentials they share, on a consent basis. This decentralized approach limits unwanted data sharing—the very issue that has driven the development of laws like the EU’s General Data Protection Regulation (GDPR).
Blockchain technology may become the cornerstone of SSI. Decentralized, public ledgers can offer much greater flexibility with reduced risk. SSI does not strictly rely on traditional accounts to establish a person’s online identity. Research and development in this area continues to accelerate.
- The advent and impact of AI
The rise of machine learning (ML) and artificial intelligence (AI) is creating more advanced opportunities for digital identity management. ML/AI solutions can analyze large, complex data sets in a short time, identifying patterns and uncovering connections that would be difficult, if not impossible, for humans to detect. These capabilities could become the foundation of future identity solutions.
AI tools can collect disparate elements of an individual’s digital identity to deliver positive verification more efficiently. Additionally, they can analyze customer behavior patterns, which can then be used to streamline future identification processes. By evaluating hundreds or even thousands of identity factors, AI has the potential to power the next generation of identity systems.
Explore the best approach for your business today
Secure digital identity solutions are no longer optional—they’re essential for any business with an online presence. Without the right approach, user experiences suffer, and risks increase, raising the potential for real, negative impacts on both users and your business. On the other hand, when you can seamlessly and efficiently authenticate a user’s identity, the user experience improves, your services become safer, and you can deliver better outcomes in every interaction.
As the digital environment and economy continue to expand and evolve, brands must stay aligned with current demands. Simple, streamlined mobile authentication makes this easier. With Telesign’s support and innovative products for digital identity verification, you can quickly enhance your service quality. Take a moment to evaluate your current approach—could there be a faster, more efficient way to achieve your goals? Connect with the Telesign team today to learn more about how you can quickly and easily enhance your digital identity strategy with our scalable solutions.